ISC2 Survey: 70% of Respondents Highly Concerned by Supply Chain Risk

ISC2 survey reveals that organizations of all sizes and sectors struggle with a shared challenge: a lack of visibility across their expansive network of third-party vendors and partners.
Levels of Concerns about Supply Chain Security | A Closer Look at the Results | The State of Supply Chain Cybersecurity Incidents | Nuances Behind the Numbers | The Biggest Challenges | Top Areas of Concern | Mitigating Supply Chain Security Risk | Taking Back Control Through Action | A Sector Snapshot of the Most Stringent Controls | Mixed Approaches to Supply Chain Risk Management | Maturity of Incident Response | Supply Chain Security Considerations for Organizations | Methodology | Related Insights
Any organization operating in the digital economy today is no stranger to supply chain risk. After 2020’s powerful one-two punch of physical (pandemic-fueled breakdowns) and digital (e.g., the SolarWinds attack) disruptions, adopting a deeper focus on supply chain stability and cybersecurity has become a must-have for mature risk management programs.
Recognizing the escalating importance of supply chain cybersecurity, ISC2 conducted a global survey of 1,062 cybersecurity professionals to gauge the current state of this pressing topic and its effects on the cybersecurity workforce and operations. Respondents worked in organizations of varying sizes: small (1–499 employees), medium (500–2,499), large (2,500–4,999) and enterprise (5,000+).
Levels of Concerns about Supply Chain Security
The survey found that 70% of respondents said their organizations are highly (i.e., very or extremely) concerned about cybersecurity risks in their supply chains. Concern is highest among respondents from enterprise organizations, where 82% report high levels of concern. In comparison, 57% of respondents from both small and medium organizations share this level of concern.
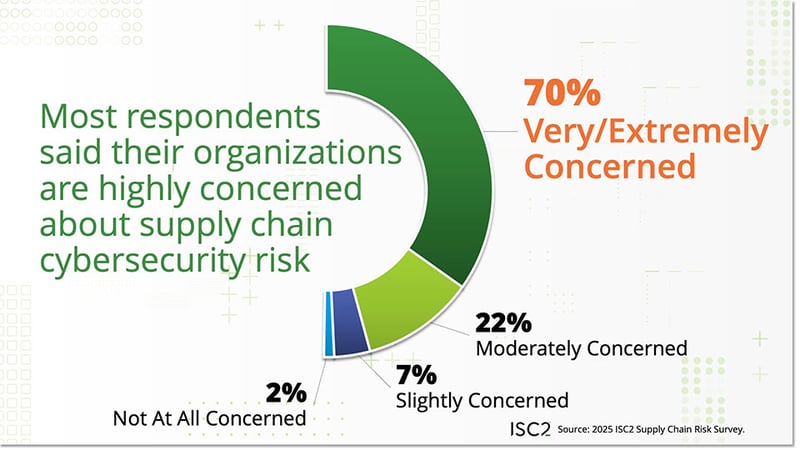
A Closer Look at the Results
Organizations that have experienced a cybersecurity incident originating from a third-party vendor or supplier are significantly more likely to report high levels of concern (75% are very or extremely concerned versus 63% among those without such incidents).
Similarly, organizations that provide software, digital services or managed solutions to other businesses are more likely to express concern compared to those that do not (72% are very or extremely concerned vs. 65%, respectively).
Concern is highest among certain sectors: 82% of financial services organizations and 81% of military and military contractor organizations report being very or extremely concerned, compared to 70% across all organizations. Healthcare, an increasingly digitalized sector reliant on an extensive third-party supply chain, is also facing significant pressure; 67% report being very or extremely concerned about cybersecurity risks in their supply chain.
The State of Supply Chain Cybersecurity Incidents
Experiencing the effects of third-party cybersecurity incidents is not rare. The survey found that 28% of participants said their organizations have experienced a cybersecurity incident originating from a third-party vendor/supplier in the past two years. Rates are highest within enterprise organizations, where 34% of respondents revealed that their organizations experienced a third-party vendor/supplier incident. Over a third (37%) of those employed in financial services organizations said their organizations had been impacted in the past two years, significantly higher than other sectors (e.g., IT Services at 20%).
Not all third-party supplier incidents have a direct impact on customers, as 47% of participants said their organizations were not impacted directly when their suppliers had a cybersecurity incident.
Nuances Behind the Numbers
Enterprise organizations are more likely to have experienced a cybersecurity incident originating from a third-party vendor or supplier, with 34% reporting being impacted in the past two years.
Those in the financial services are more likely to say their organizations have been directly impacted by a supply chain security incident compared to the total (37% vs. 28%, respectively).
The Biggest Challenges
When asked what they think is the biggest challenge in securing the supply chain against cyber threats, respondents highlighted the lack of visibility, transparency or control of suppliers as dominant challenges to securing supply chains. Many respondents are also concerned about the complexity of their supply chains, noting that they are not aware of their vendors’ vendors, or of all the possible points of entries that exist when multiple players are involved. As one respondent emphasized,

Vendor-related risks, such as poor or unknown vendor cybersecurity practices and having to trust vendors without the ability to verify their claims, are also concerns among participants. Respondent statements such as “we have to trust them,” “trust but can’t verify,” “blind trust,” etc., are similar to those related to lack of visibility in supplier practices, but this theme is more about trusting that the vendor will be transparent.
Top Areas of Concern
Nearly two-thirds of respondents said that data breaches are the most disruptive cybersecurity threat (64%) to their organization’s supply chain. Malware or ransomware rank second, at 52%, while software vulnerabilities in supplier products rank third, at 51%.

While percentages are comparatively lower for unauthorized access through third-party credentials and lack of visibility into supplier cybersecurity practices, more than a third also rank these as disruptive threats (37% and 35%, respectively). Supply chain threats are not necessarily external ones; 29% rank insider threats from vendors as being disruptive for their organizations.
Mitigating Supply Chain Security Risk
One of the biggest challenges customers face with their supply chains is a lack of information about the inherent risk a supplier or a downward chain of suppliers poses to the organization. Risk assessments and supplier evaluations are essential tools to establish visibility of a supply chain’s security posture and its risk factors.
Most organizations (70%) conduct third-party risk assessments on a regular schedule, such as at the time of contract renewal or annually. Additionally, 49% of organizations take a close look during initial evaluation/onboarding, 26% when incidents have occurred and 25% when monitoring tools alert them to a third-party threat.

Organizations evaluate the cybersecurity practices of their suppliers at varying intervals: 45% conduct assessments annually, 10% semi-annually, 17% quarterly, and 12% monthly. Notably, evaluation frequency does not differ significantly by organization size or industry.
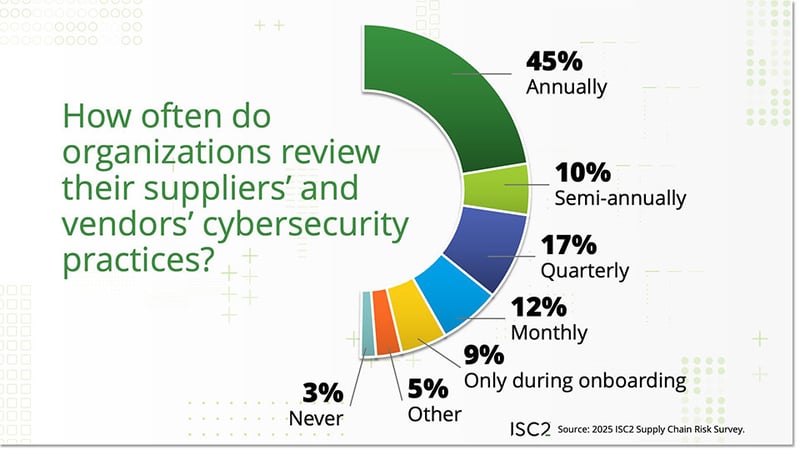
Among survey respondents, 9% said their organizations evaluate supply chain vendors only during initial onboarding, highlighting a crucial issue. A multi-year supplier agreement can expose a customer to deteriorating security practices and leave them with a false sense of security based on a one-time snapshot of the supplier's processes.
Taking Back Control Through Action
Organizations are overcoming the visibility obstacle by requiring vendors to provide validation of numerous cybersecurity controls during the procurement process. As one survey respondent noted,

Over three quarters (77%) of participants cite compliance with standards (e.g., ISO 27001, NIST, SOC 2) as their top requirement, followed by security audits/attestations/assessments (71%), multi-factor authentication/secure access protocols (62%) and incident response and breach notification procedures (61%). Only 5% said their organizations do not require any controls.
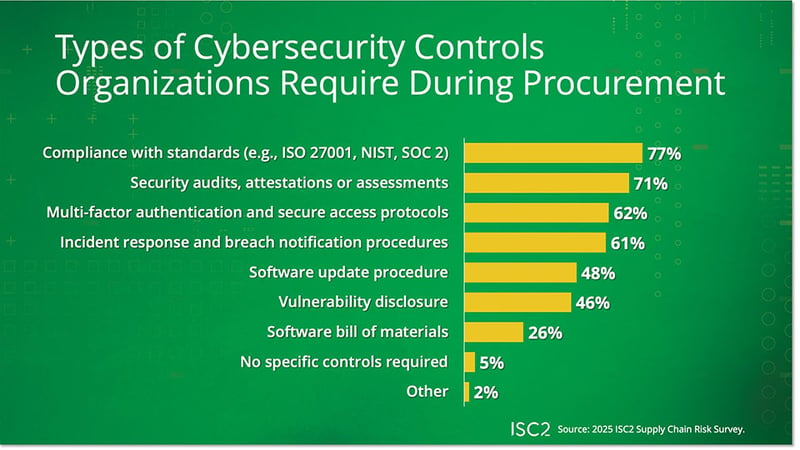
A Sector Snapshot of the Most Stringent Controls
Enterprise organizations are more likely to require a wider range of security controls compared to smaller organizations. Sector analysis shows that financial services and military/military contractor organizations have some of the highest control requirements among all industries.
Financial services organizations require these controls at significantly higher rates than other sectors:
- Compliance with standards such as ISO 27001, NIST, or SOC 2 (84% vs. 77% across all participant industries)
- Security audits, attestations, or assessments (80%)
- Incident response and breach notification procedures (75%)
- Multi-factor authentication and secure access protocols (73%)
- Vulnerability disclosure (56%)
Military and military contractor organizations report significantly higher requirements for the following controls:
- Compliance with standards (ISO 27001, NIST, SOC 2) (87%)
- Software update procedures (65%)
- Software bill of materials (41%)
Mixed Approaches to Supply Chain Risk Management
Control from the beginning of a third-party vendor relationship is one thing; ongoing risk management is another. Organizations have mixed approaches to supply chain risk management. Over half (54%) of respondents report that their organization has a dedicated risk management program. This percentage jumps significantly to 70% when looking at enterprise organizations.
Many organizations approach supply chain risk management in a less formal manner—or, surprisingly, not at all. Specifically, 20% rely on contracts/service level agreements (SLAs), while 16% address risks on a case-by-case basis. In addition, 10% have no formal program or approach to managing supply chain risk, of which 8% are in the process of developing one, while 2% currently have no formal program and no plans to develop one.
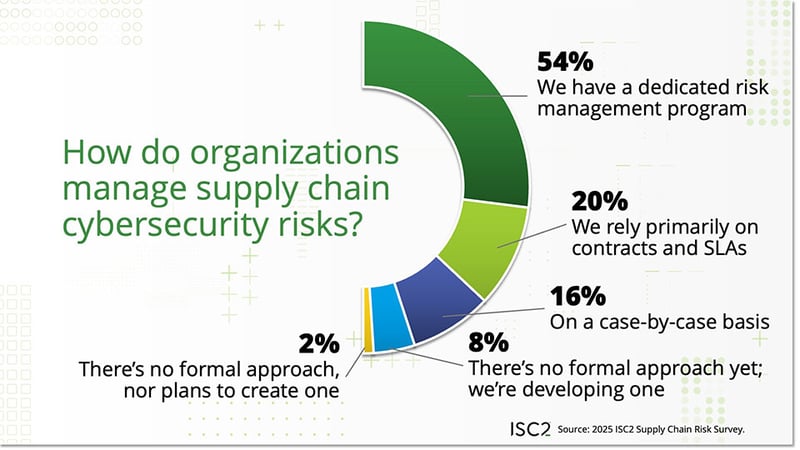
Maturity of Incident Response
Among organizations that provide software, digital services or connected managed services to other organizations, a large majority (83%) report having formal incident response policies with detailed communication plans and timelines to notify customers in the event of a breach or cybersecurity incident. Only 6% said their organization definitely does not have formal IR policies, while 11% said they are not sure.
Among those who work at vendor/supplier firms with formal incident response policies, most who shared details indicate that their policies are aligned with standards and regulations, including industry and government-specific regulations around incident reporting, such as:
- ISO/IEC 27001 and 27035
- GDPR
- NIST (SP 800-61, 800-53)
- DORA NIS2
- HIPAA
- SOC 2 PCI-DSS, FedRAMP
- DFARS 7012, ASD Essential Eight, UK NCSC
Supply Chain Security Considerations for Organizations
While there are noted variances among the cybersecurity professionals who participated in the survey, one thing is certain: You can’t protect what you can’t see. Better visibility breeds better control of third-party security risk. As one survey respondent pointed out, the biggest challenge in securing the supply chain against cyber threats is "visibility of whether what we are told by suppliers actually matches reality."
It is incumbent upon cybersecurity organizations to prioritize supply chain security, especially given that there is no longer a perimeter of defense for any organization operating in the connected, digital economy. AI tools are only compounding the supply chain threat.
Advice for organizations and cybersecurity professionals:
- Third-Party Risk Assessments: As the software supply chain has become increasingly important for organizations, third-party risk assessments have emerged as a common practice to identify potential security issues. These assessments often include vulnerability scans and checks for misconfigurations.
- Critical Infrastructure Risk Management: Critical infrastructure (CI) attacks can have a substantial impact on public safety, with knock-on impacts that ripple through other CI sectors due to deeply intertwined supply chains. Prioritizing CI supply chain security through formal onboarding and ongoing assessments is imperative.
- A Zero Trust Architecture: Security is not just about guarding the perimeter anymore; it's about having security protocols at every turn. A Zero Trust approach provides constant verification that each person is where they should be and accessing only what they need and are authorized to access—from on-premise to cloud.
- Vendor Contract Reviews: Reviewing and evaluating vendor agreements is an important task for cybersecurity teams and budget holders. Serving as an important supply chain stress test, it provides an opportunity to identify and address weaknesses and changing needs, ensuring that a good contract with clear deliverables and expectations is part of a cybersecurity defensive strategy alongside the people and the technology.
- Cybersecurity Skills Development: Cybersecurity governance, risk and compliance (GRC) professionals who use frameworks to integrate security and privacy within organizational objectives can turn to professional certifications, such as ISC2’s CGRC, to better enable their organization’s stakeholders to make informed decisions regarding data security, compliance, supply chain risk management and more.
For more information about maturing your supply chain security strategy, join our two-day virtual event: ISC2 Spotlight on Supply Chain Security on December 3-4, 2025. Register here for Restoring Confidence from Upstream to Downstream.
Methodology
An online survey was conducted among 1,062 respondents who work in a role with cybersecurity responsibilities.
Participants had to be employed at an organization that currently partners with any third-party/external vendors or suppliers of IT or security services (e.g. organization software, digital services and/or connected managed equipment, etc.). Around half (56%) of participants work at organizations that are also suppliers of IT/security products or services.
Data was collected from August 12 to 28, 2025.
Related Insights
- Resources for Addressing Supply Chain Cybersecurity Challenges
- #ISC2Congress: License to Secure – A People-Centric Approach to Managing Cumulative Third-Party Data Breach Risk
- Why Digital Identities Are Important and How to Safeguard Them
Levels of Concerns about Supply Chain Security | A Closer Look at the Results | The State of Supply Chain Cybersecurity Incidents | Nuances Behind the Numbers | The Biggest Challenges | Top Areas of Concern | Mitigating Supply Chain Security Risk | Taking Back Control Through Action | A Sector Snapshot of the Most Stringent Controls | Mixed Approaches to Supply Chain Risk Management | Maturity of Incident Response | Supply Chain Security Considerations for Organizations | Methodology | Related Insights