How Bechtel National‘s graded approach to cybersecurity supply chain risk management turned a complex challenge into a practical, scalable solution for organizations of all sizes.
As part of the recent ISC2 Spotlight on Supply Chain Security, engineering specialist Bechtel National’s Information System Security Officers—Jay Reinhardt, CISSP, CGRC, and Nick Volosin, C-SCRM Lead—shared practical insights and lessons learned along the way of developing and implementing the organization’s cybersecurity supply chain risk management (C-SCRM) program.
Reinhardt set the stage by giving the audience “a place to begin” to show them “how to use a graded approach to make this big, scary problem of supply chain management manageable and practical.” Indeed, supply chain security is daunting. The 2025 ISC2 Supply Chain Risk Survey found that 70% of respondents said their organizations are highly (i.e., very or extremely) concerned about cybersecurity risks in their supply chains. Concern is highest among respondents from enterprise organizations, where 82% reported high levels of concern. In comparison, 57% of respondents from both small and medium organizations shared this level of concern.
Bechtel’s C-SCRM Lead, Volosin, walked through how the organization developed its leveled approach to address supply chain security concerns while tackling a two-fold challenge: protecting critical systems while complying with stringent requirements, all without inflating costs or creating unnecessary complexity.
While Reinhardt and Volosin manage supply chain risk for a high-level, multi-billion-dollar nuclear waste processing plant in construction, their pragmatic advice is applicable across all organizations. That’s because, fundamentally, “a one-size-fits-all approach simply doesn't work,” said Volosin. Instead, a graded approach that can be tailored to suppliers of all sizes is more effective.
Why a One-Size-Fits-All Approach to Supply Chain Risk Management Doesn’t Work
Before diving into Bechtel’s C-SCRM approach, Volosin acknowledged a foundational truth: not all suppliers pose equal risk. He explained, “Some suppliers deliver mission-critical software or hardware that sits deep inside our environment, transmitting sensitive data or performing life-critical processes. Others deliver things like office supplies or commercial commodity IT services.”
It is a crucial insight, then, that “Treating these suppliers as if they present the same risk simply isn't realistic.” It is also counterproductive. “When blanket requirements are applied, for example, demanding a secure development lifecycle package from a vendor selling PDF editing software, we create new problems,” he added, warning that smaller vendors “cannot realistically produce documentation meant for the high-value system integrators.”
According to Volosin, applying one-size-fits-all requirements:
- Overburdens low-risk suppliers
- Creates unnecessary compliance work
- Reduces focus on high-risk areas
Risk Drives Rigor for Supply Chain Risk Management
To address these challenges, Bechtel adopted a C-SCRM strategy that is centered on the principle of “risk drives rigor.” This principle is the foundation of what Reinhardt, Volosin and their team call the graded approach: “a structured way to scale expectations based on actual risk.” He elaborated that, “The amount of scrutiny we apply must reflect the real-world mission or business impact if that supplier, or more specifically, if what the supplier provides, was compromised?”
The Seven Steps of a Graded Approach to C-SCRM
Implementing this model requires deliberate planning. Here is a step-by-step guide to how the Bechtel team built it into their organization.
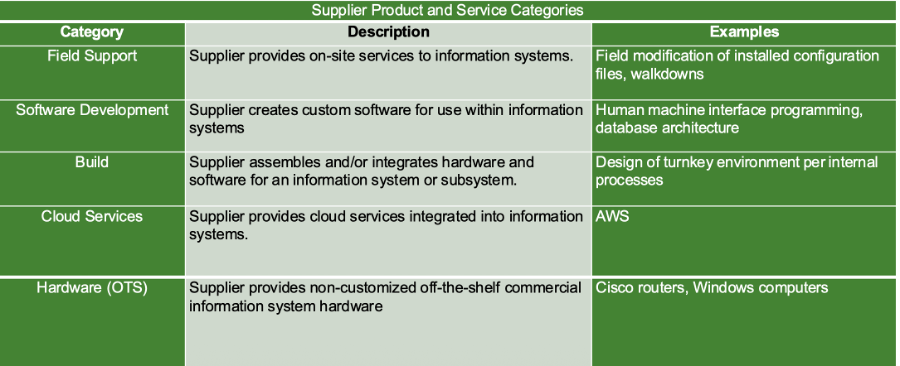
Step 1: Define Product and Service Categories
Group products and services based on cybersecurity relevance to enable consistent, repeatable decisions. Keep categories broad but useful and collaborate across procurement and engineering.
Step 2: Establish Cybersecurity Impact Levels (SILs)
Create Cybersecurity Impact Levels (CIL): High, moderate or low. These are simple and understandable levels that “identify the level of cybersecurity rigor expected to be applied to your suppliers,” said Volosin.
Factors to consider:
- Data sensitivity or system criticality
- Supplier access (physical and logical)
- Mission or safety impact
Step 3: Define Requirements for Each Impact Level
This is the step where the team identified all their internal and external cybersecurity requirements to determine how to apply them. The goal is to focus on how the requirements fit into those cybersecurity impact levels. Volosin advised translating CILs into actionable requirements, split into two complementary types: technical requirements (e.g., verified through product inspection) and programmatic requirements (e.g., internal supplier processes).
Step 4: Identify the Subset of CIL Requirements Appropriate to Each Category
This step is “about selecting the right requirements for each previously defined product or service category based on the assigned impact level,” said Volosin.
Step 5: Embed the Graded Approach in Procurement Process
A smart framework delivers value only if it is embedded in the real procurement process to reduce friction, speed procurement and target cybersecurity involvement where it’s truly needed.
This step may include the following:
- Pre‑screening suppliers to engage only those capable of meeting the required rigor
- Providing clear instructions to those who generate requisitions (e.g., through training or quick guides)
- Restricting procurement methods that can’t support C‑SCRM
- Embedding cybersecurity expertise throughout the lifecycle
- Leverage existing controls and processes wherever possible
Step 6: Apply the CIL and Category to Every Requisition
This step is about creating centralized visibility of all purchases within C‑SCRM scope via a tracking database. With clear definitions and examples, cybersecurity can ultimately assign categories to maintain consistency. As the process matures, CIL and category assignments become fast, repeatable and defensible. A cybersecurity subject matter expert should assign the CIL and consult with the requesting organization to assign category.
Step 7: Improve Over Time (Continuously)
It is important to keep in mind that C‑SCRM is a living program and that the seventh step is “never really the final step,” said Volosin. "This is where your C-SCRM program becomes sustainable, efficient and increasingly accurate,” even as your supply chain requirements change. It is important to keep in mind that, “Your approach must also evolve with some mechanisms to monitor for improvement.”
Suppliers change, requirements evolve, processes mature and threats shift. Against that backdrop, Volosin recommends building mechanisms for continuous improvement, such as:
- Monitor procurement cycles and capture lessons learned
- Watch for signals of mis‑grading
- Expect resistance and offer assistance, not enforcement
- Maintain transparency with suppliers
For more insights on managing supply chain risk, visit Resources for Addressing Supply Chain Cybersecurity Challenges.
Related Insights



