The recent virtual Spotlight event delivered a two-day in-depth look at issues relating to governance, risk and compliance, with NIST’s updated cybersecurity framework and how it can support organizations at the centre of the conversation.
The vast majority of professionals working in the cybersecurity industry will have heard of The National Institute of Standards and Technology’s Cyber Security Framework (better known as the NIST CSF). Although very few of us are able to recite big chunks of the content, this does not prevent us from seeing it as a go-to reference model of good practice for cyber security. And in February 2024 NIST announced a major update to the CSF, bringing it to version 2.0.
This was one topic of conversation at ISC2’s recent Governance, Risk and Compliance Spotlight event, where host Brandon Dunlap was joined by Daniel Eliot and Stephen Quinn from NIST for an exploration of what is new in release 2.0 of the NIST CSF.
 Eliot set the scene with a one-sentence description of the CSF: “Guidance that helps organizations – regardless of size, sector or maturity – better understand, assess, prioritize and communicate their cybersecurity efforts”. He also noted that unless you run federal networks or critical infrastructure in the U.S. or have some kind of commercial relationship that mandates working to the CSF, the guidance is used entirely voluntarily by the vast majority of those who adopt it, as a purely advisory path to best practice. This done, the presenters then walked through the five key changes between versions 1.1 and 2.0 of the CSF.
Eliot set the scene with a one-sentence description of the CSF: “Guidance that helps organizations – regardless of size, sector or maturity – better understand, assess, prioritize and communicate their cybersecurity efforts”. He also noted that unless you run federal networks or critical infrastructure in the U.S. or have some kind of commercial relationship that mandates working to the CSF, the guidance is used entirely voluntarily by the vast majority of those who adopt it, as a purely advisory path to best practice. This done, the presenters then walked through the five key changes between versions 1.1 and 2.0 of the CSF.
Governance of Risk Management Processes
“We want to make a key distinction between governance management and risk governance”, said Eliot, noting that the revised framework has an entirely new function around governing risk management processes. “Risk governance seeks to set the criteria and the expectations by which risk management, including cybersecurity will be conducted. It provides the transparency, responsibility and the accountability that enables managers to acceptably manage risk”.
Supply Chain
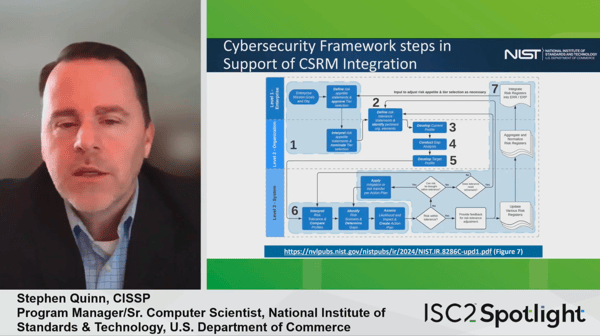
Given the huge growth in supply chain threats – and the growth in awareness of those threats – it was no surprise to hear that supply chain risk has been elevated in importance and integrated across the new framework. Eliot pointed to NIST Interagency Report (IR) 8286 as a useful reference for anyone needing to know more, particularly in the realm of integrating enterprise risk management with cybersecurity risk management, and Quinn expanded on the supply chain concept: “The implementation example we have here is with respect to, I think you'll notice in the govern function, in the CSF we included a good deal of supply chain risk management, third party and counterparty risk is addressed inside that. We didn't just leave it at an outcome statement at the subcategory level, we also included specific implementation examples and we tried to make these, again, practical and actionable”. The implementation examples referenced later reflect this, with concepts such as “establish a strategy that expresses the objectives of the cybersecurity supply chain risk management program” and “alignment between functions that contribute to cybersecurity supply chain risk management, such as cybersecurity, IT, operations, legal, human resources, and engineering”.
Addressing Specific Threats and Technology Shifts
It is no accident that ISC2 has written a good amount about Operational Technology (OT) over the last few months, as it is clearly a growing threat area – as was confirmed by Eliot: “over the last few years, we're seeing significant increase in threat actors targeting OT systems as they are increasingly … more connected over the internet”. The new CSF therefore takes account of this; “we have new categories and subcategories such as platform, security, technology infrastructure resilience”, said Eliot, “to address evolving risks and technologies … and we know that organizations are leveraging more varied platforms these days to include both virtual and on prem systems as well as OT and IoT”.
Rapid Adoption
 “We focused on how organizations can more rapidly implement and improve their cybersecurity posture”, said Eliot. Quinn backed this up with a demo of the new-look framework, showing high-level links to a variety of “quick start” guides including ones for small businesses, supply chain risk management, enterprise risk management, plus a 30-page set of implementation examples that provide a comprehensive set of starting points for adopting the framework.
“We focused on how organizations can more rapidly implement and improve their cybersecurity posture”, said Eliot. Quinn backed this up with a demo of the new-look framework, showing high-level links to a variety of “quick start” guides including ones for small businesses, supply chain risk management, enterprise risk management, plus a 30-page set of implementation examples that provide a comprehensive set of starting points for adopting the framework.
From a Single Document to a Wider Resource Pool
The focus has also been shifted away from a single, monolithic document to a collection of materials that include implementation examples, quick start guides, organizational profile templates and databases that ease reference into and integration of the CSF. As Quinn pointed out: “One of the things that we found lacking in CSF 1.1 was implementation resources. There was no implementer guide, no quick start”, going on to mention the document shift from one to many: “Informative references were embedded in the CSF 1.1 prior to the release of CSF 2.0; we have removed them from the core, and we've removed them from the static document, so that we can grow them over time”. Eliot also mentioned the existence of a useful spreadsheet that enlightens those reading this who are familiar with CSF 1.1 regarding the new elements in 2.0 and how the two versions map together.
Wrapping Up
NIST CSF 2.0 is a substantial reference. The collection of implementation examples cited earlier runs to 30 pages. The collection of informative references, which is a generated-on-the-fly spreadsheet, ran to over 2,000 references when we downloaded it and is only going to get bigger. The substantial size is not necessarily a barrier to using NIST 2.0, because the fact that the design has been deliberately changed from a big, single document to an orchestrated set of connected resources makes it usable, and consumable in manageable chunks.
Related Insights
- On-demand access to the ISC2 Spotlight for registered attendees
- Register now for ISC2 Security Congress 2025
- CGRC – Governance, Risk and Compliance Certification


