An effective cybersecurity strategy requires many moving parts, skills and stakeholders to come together to deliver it. Grant Hughes, CISSP, CCSP, SSCP, CC shares his guidance for defining a strategy based on his first-had experience.
 The song called Any Road by George Harrison is a good reminder of
why a strategy is important. He sings ‘If you don’t know where you’re
going, any road will take you there.’ The lyrics are a stark reminder,
perhaps even a warning, that if you do not start with a defined strategy,
purpose and objective, you will run into challenges down the line.
The song called Any Road by George Harrison is a good reminder of
why a strategy is important. He sings ‘If you don’t know where you’re
going, any road will take you there.’ The lyrics are a stark reminder,
perhaps even a warning, that if you do not start with a defined strategy,
purpose and objective, you will run into challenges down the line.
Defining a cybersecurity strategy requires knowledge and skill. Defining a world-class cybersecurity strategy that is crystal clear, concise and aligned to business objectives, requires cybersecurity expertise. It also needs accurate information and a solid understanding of the threat landscape and business context.
Based on my experience, we’ll look at where to start, what to do and what to avoid when developing your cybersecurity strategy.
Cybersecurity Strategy Development Framework
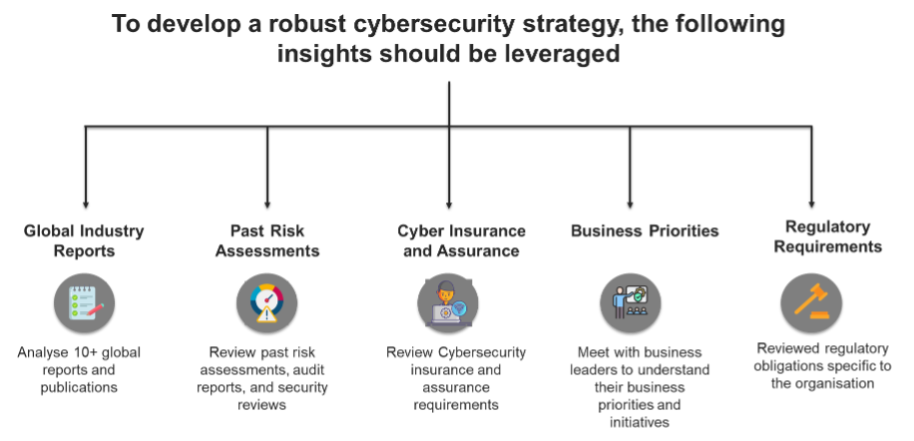
A cybersecurity strategy must be developed by considering various strategic inputs. In cybersecurity, it makes sense for those strategic inputs to the following five inputs:
- Global Industry Reports:This includes research reports, vendor white papers and academic research papers. Any reputable industry insights should be reviewed and analysed to gain insights and an understanding of the global threat landscape. The focus must be on good quality reputable reports and research
- Past Risk Assessments: The current cybersecurity posture of your organisation must drive the cybersecurity strategy. This insight can be gained by reviewing audit reports from the past 12-18 months, penetration testing reports, security reviews and vulnerability management reports. Any past assessment that provides insight into the risk posture should be leveraged
- Cyber Insurance and Assurance Requirements: An understanding of your organisation’s insurance requirement is important as this will reveal gaps or areas of weakness. As a result, it will influence the strategy and priorities
- Business Priorities: This is arguably the most important, and also often overlooked input. You must understand what your organisation’s priorities are. For example, if you find yourself working for a municipality and your business strategy is to start a Smart City initiative next year, this will impact your OT cybersecurity strategy and must be considered. The primary purpose of cybersecurity is to support business objectives. This input into the strategy is vital
- Regulatory Requirements: It is imperative to understand the regulatory obligations of your organisation and translate that into cybersecurity initiatives. For example, if GDPR or PCI-DSS apply to you, it will impact the cybersecurity initiatives and priorities. If your organisation maintains an ISO 27001 certification, that must be considered as it will influence the strategy
Common Mistakes to Avoid When Defining a Cybersecurity Strategy
- Do not allow technology vendors to develop your strategy. Technology vendor roadmaps and insights should inform your thinking, but caution should be exercised not to allow vendors to unduly influence your cybersecurity strategy
- Do not define the cybersecurity strategy in isolation with the cybersecurity team only. Present the strategy to other IT teams and business leaders for input. You are more likely to gain the support of stakeholders if they believe they were part of the process
Guidelines for Developing a Robust Cybersecurity Strategy
- Take your stakeholders on the journey with you. Adopt a consultative approach by starting with the cybersecurity team, then gradually including more stakeholders in the process such as other internal IT teams, business stakeholders, and industry experts. Note that these industry experts should not be your technology providers, but rather trusted advisors who have no conflict of interest
- Understand that people are at the centre of what we do. Security awareness, culture, and governance should be a core theme of your cybersecurity strategy
- Identify and prioritise the top cybersecurity risks as it pertains to your business. For example, if you have fifteen critical items to address, but only receive a budget for five items, you should have a clear methodology on how you would select those five priority items. Your approach should be based on risk, the Pareto Principle, and a cost-benefit analysis
- Consult experts. Developing a meaningful and robust cybersecurity strategy is a skill. If you do not have this skill, consult experts that do while you learn and upskill
Adapting to Change is Imperative
In 1996, a group set out to climb Mount Everest. They had all the right equipment and they were well trained and fit, but on Everest there is a rule: If climbers do not reach the summit by a certain time of the day, they must abandon the attempt. This day, there was a traffic jam of sorts as four different expeditions all attempted to reach the summit, these climbers did not reach the summit by the specified time. At this point, they should have turned around, but they did not. They reached the summit too late and had to climb down in the darkness and were caught unprepared by an unexpected storm. Sadly, they all died during the attempt.
This tragedy offers a valuable lesson for security teams. They commit to a three-year plan or an eighteen-month road map. As time passes, the business context changes, the threat landscape evolves and evidence starts to emerge that the current strategy is a bad idea. At that point, the team should stop, reevaluate and readjust the strategy. It is often difficult to admit that mistakes have been made, so security leaders may continue heading in the wrong direction. However, if it becomes apparent that a cybersecurity strategy is no longer effective or appropriate, cybersecurity leaders have a responsibility to rectify it.
It is therefore imperative not to view the cybersecurity strategy as a once-off exercise. The threat landscape is continuously evolving and therefore the cybersecurity strategy must be reviewed regularly.
Conclusion
The cybersecurity strategy provides a forward-looking view into what you are planning as a cyber leader and why you are doing it. Consider the audience, tailor the content using visuals, stories and analogies. For the stakeholders who appreciates the detail, there should always be a detailed strategy document supported by tactical plans. However, for the senior decision makers, you need to keep it succinct, visual, factual and presentable in under ten minutes.
- ISC2 Skill Builders for Security Operations - These courses are free for ISC2 members. There is a nominal fee for non-members
- ISC2 Think Tank Webinars provide helpful insights into the latest cybersecurity trends, thought leadership and best practices. There are a variety of webinars available free of charge on the ISC2 website on topics like emerging technologies and strategies for CISOs in a transforming job market


