 Somnath Shukla, CCSP
Somnath Shukla, CCSP
In today’s interconnected world, the security of our digital identities and data is paramount. As cyber threats continue to evolve and become more sophisticated, relying solely on traditional password-based authentication methods is no longer sufficient. This is where Multifactor Authentication (MFA) steps in, providing an additional layer of security to protect our online accounts and sensitive information. In this blog, we will delve into the concept of MFA, how it works, and its importance of safeguarding our digital lives.
Understanding Multifactor Authentication
Multifactor Authentication, also known as MFA or 2FA (Two-Factor Authentication), is a security process that requires users to provide two or more different authentication factors before granting access to a digital resource. These factors fall into three main categories:
- Something You Know: This is the traditional username and password combination. It is a piece of information that only the user should know. However, passwords can be vulnerable to various attacks, such as brute force, phishing, and credential stuffing.
- Something You Have: This factor involves something the user physically possesses, like a smartphone, a hardware token, or a smart card. Access to the digital resource is granted when the user presents this item.
- Something You Are: This factor relies on biometric data unique to the individual, such as fingerprints, facial recognition, or iris scans. Biometrics provide a highly secure means of authentication, as they are difficult to replicate.
How Multifactor Authentication Works
The key principle behind MFA is combining factors from at least two of the above categories to create a robust authentication process. Here’s a step-by-step breakdown of how MFA works:
- Initiation: When a user attempts to access a protected digital resource, they are prompted to provide their primary authentication factor, usually a username and password.
- Secondary Authentication Factor: Once the primary factor is verified, the user is prompted to provide a secondary factor. This could be something they have, like a one-time code sent to their mobile device, or something they are, like a fingerprint scan.
- Authentication Request: The secondary factor is then submitted along with the primary factor for authentication. Both factors are analyzed by the authentication system to determine if they match the user’s stored credentials.
- Access Granted/Denied: If both factors match, access is granted, and the user gains entry to the digital resource. However, if any factor fails to authenticate, access is denied, and the user is prevented from entering.
The Importance of Multifactor Authentication
MFA offers several crucial benefits in the realm of cybersecurity:
- Enhanced Security: MFA adds an extra layer of protection beyond passwords, making it significantly more challenging for malicious actors to gain unauthorized access. Even if a password is compromised, the attacker would still need the secondary factor to breach the account.
- Mitigation of Credential Theft: With the rise of data breaches and password leaks, MFA helps mitigate the risk associated with stolen or weak passwords. Even if an attacker has your password, they would be unable to access your account without the second factor.
- Phishing Resistance: MFA is resistant to phishing attacks because attackers cannot easily replicate the secondary factor, such as a one-time code generated by an authentication app or hardware token.
- Compliance Requirements: Many industries and regulatory bodies require the use of MFA to meet specific security and compliance standards. Implementing MFA can help organizations avoid legal and financial penalties.
- User-Friendly: MFA can be user-friendly when implemented correctly. Modern authentication apps and methods are convenient and quick, making them a viable option for most users.
Common Multifactor Authentication Methods
There are various methods and technologies used in MFA including:
- Authentication Apps: Specialized apps, like Microsoft Authentication, Google Authenticator or Authy, generate time-based one-time codes for the secondary factor.
- Biometrics: Devices equipped with fingerprint scanners, facial recognition cameras, or iris scanners use biometric data as the secondary factor.
- Hardware Tokens: Physical devices, such as USB security keys, generate codes or require physical interaction for authentication.
- Smart Cards: These cards contain embedded chips that store authentication data and require insertion into a card reader.
- Push Notifications: Users receive a notification on their registered mobile device, and they confirm or deny access with a single tap.
- SMS or Email Codes (Obsolete): Users receive a one-time code via SMS or email, which they must enter alongside their password. I would not recommend to use sms or email for MFA.
Implementing MFA IN IdP
As a Developer you can implement MFA using ASP.Net Identity or any other framework. Below is the typical request response flow.
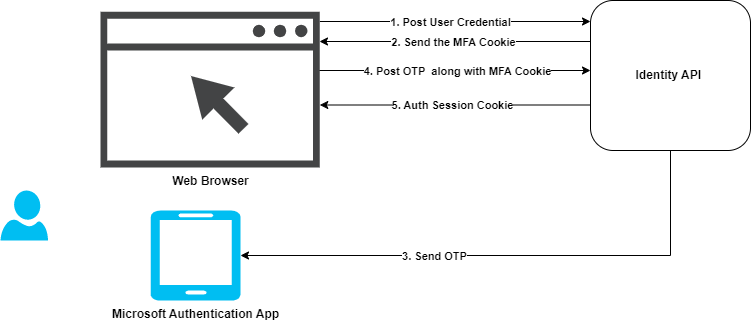
MFA is implemented at IdP level. Now a days most of application uses OpenID Connect for Authentication and Oath2 for authorization. MFA is must irrespective of what authentication protocol you uses in your application where its SPA, Mobile or Web.
Conclusion
In a digital landscape where cyber threats are constantly evolving, Multifactor Authentication (MFA) stands as a critical defense mechanism. By requiring users to provide two or more authentication factors from different categories, MFA significantly enhances security, mitigates the risk of password-related breaches, and offers resistance to phishing attacks. It is a fundamental component of modern cybersecurity strategies, protecting not only individual accounts but also the sensitive data and assets of organizations and institutions. As we continue to embrace digital technologies in our daily lives, the adoption of MFA is essential in safeguarding our digital identities and preserving the integrity of our online interactions.
Somnath Shukla, CCSP is a Multi Cloud Solution Architect (Public and Private), Certified Cloud Security Professional, Certified Kubernetes Administrator and life-long learner. He has 17+ years of experience in Azure, Nutanix, Azure Stack HCI, VMware VCF/VCD, GCP and AWS.


