Enterprises are abandoning traditional business models and adopting digital transformation at a fast pace, embracing cloud, multi-cloud and/or hybrid cloud environments. The adoption rate of cloud applications has been dramatic in recent years, with organizations of all sizes moving to cloud-based delivery models.
As enterprises embrace cloud computing, cloud security becomes a top concern. This is especially evident in the surge in phishing attacks against cloud services, many of which have led to massive data breaches. As a result, IT teams are seeking streamlined methods of centrally defining and enforcing access controls to manage security and compliance in a consistent manner across their cloud and on-premises applications.
Traditionally, organizations have relied on Virtual Private Networks (VPN), on-premises Single-Sign On (SSO) and Web Access Management (WAM) solutions to control authentication and authorization to corporate resources. With the proliferation of cloud-based apps and distributed computing models, these legacy solutions can no longer meet the needs of modern Identity and Access Management (IAM).
What is IAM?
According to Gartner, Identity and Access Management (IAM) “is the discipline that enables the right individuals to access the right resources at the right times for the right reasons.”
A more detailed definition of IAM is the one provided by ISC2 in the CCSP CBK: “IAM includes people, processes, and systems that manage access to enterprise resources by ensuring that the identity of an entity is verified and granting the correct level of access based on the protected resource, the assured identity and other contextual information.” Modern IAM is based on digital identities and authentication.
NIST SP 800-63 defines that “digital authentication establishes that a subject attempting to access a digital service is in control of one or more valid authenticators associated with that subject’s digital identity.” For cloud services where return visits are applicable, successful authentication provides reasonable risk-based assurances that the subject accessing the service today is the same as that accessed the service previously.
“In a world defined by our use of technology, how we are identified digitally is important. Our digital identities and the credentials that protect them define how we work, interact with each other, access technology, execute transactions, and so much more,” says Julie Smith, Executive Director at Identity Defined Security Alliance
Digital identity presents a technical challenge because this process often involves proofing individuals over an open network, and involves the authentication of individuals over an open network to access digital services. The processes and technologies to establish and use digital identities offer multiple opportunities for impersonation and other attacks.
There is an increased interest in strong user authentication, as more and more regulations, such as GDPR, the European Payment Directive (PSD2), and standards, such as PCI DSS, oblige strict security requirements for protecting personal information, for electronic payments and the protection of consumers’ financial data.
Methods of authentication
Authentication establishes confidence that an individual has possession of one or more authenticators bound to the credential. Authentication does not determine the user’s authorizations or access privileges – for example, what they are allowed to do once they have successfully been allowed to access a digital service.
The classic paradigm for authentication systems identifies three factors as the cornerstones of authentication:
- Knowledge factor (“something you know”): The system accepts you if you show that you know a certain bit of information. Examples include PINs, answers to security questions, tax return details, etc.
- Possession factor (“something you have”): The system accepts you if you can prove that you have a certain physical device on you. Examples include devices such as smartcards, mobile phones and USB keys.
- Inherence factor (“something you are”): The system accepts you by using a biometric comparison. Examples include fingerprint scanners, retina scanners, voice recognition, and behavioral biometry.
Multi-factor authentication (MFA) refers to the use of more than one of the above factors. The strength of authentication systems is largely determined by the authentication technology deployed and the number of factors incorporated by the system — the more factors employed, the more robust the authentication system. With increasingly complex access environments and more access points than ever before, organizations have every reason to add multi-factor authentication.
In addition to MFA, organizations are adopting passwordless authentication, such as FIDO or Windows Hello, which eliminates the use of a textually based password. Instead of passwords, proof of identity is achieved by replacing the password with other methods of authentication. Passwordless authentication can provide varying levels of assurance and convenience based on how it is implemented, and it has gained traction because of its benefits in streamlining the user login experience and overcoming the inherent vulnerabilities of legacy passwords.
Technological innovations, such as the proliferation of mobile devices with integrated biometrics, geolocation, and other sensors, have led to the development of ‘adaptive’ or ‘contextual’ authentication. By assessing a range of attributes such as location, network or device, type of transactions and historical data, adaptive authentication can verify a person’s identity to a reasonable degree when they log into an application. In fact, it can do so without the user having to take any action, which is why this method is increasingly popular.
What can go wrong?
Weak or improper identity management increases risk. The vast majority of data breaches making headlines are the result of poor identity management. These breaches often leverage weak identity management, such as weak or previously compromised passwords, not leveraging multi-factor authentication and single sign-on or leaving standing privileges open.
The numbers are compelling:
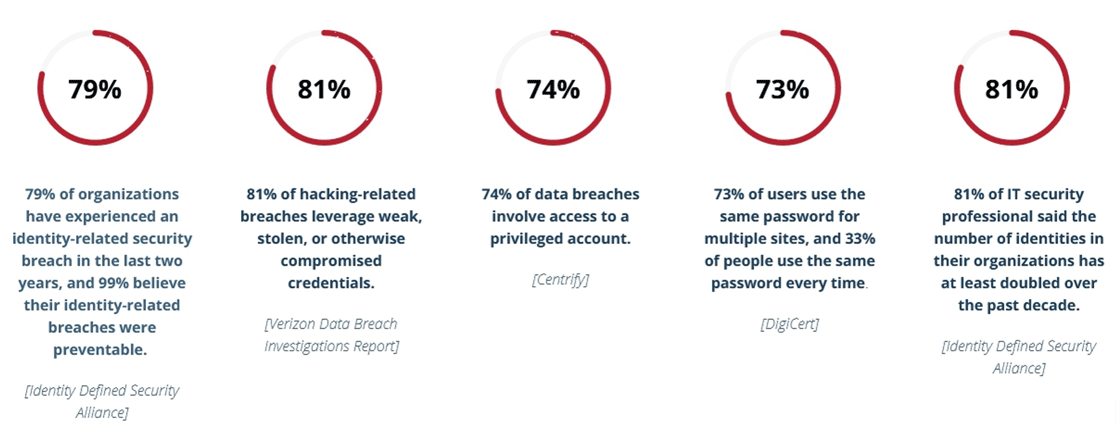
Figure 1: Identity Management and Security by the Numbers. Source: Identity Defined Security Alliance
The role of a certified and experienced cloud security professional
In an era where corporate boundaries have blurred and traditional perimeter-based security solutions are not adequate to protect sensitive assets, a certified and experienced cloud security professional has an important role to play in establishing a strong IAM program. Within cloud environments, services should include strong authentication mechanisms for validating users’ identities and credentials.
The cloud security professional should ensure that the four pillars for an enterprise wide IAM are enforced and adhered to:
- Provisioning and de-provisioning – create accounts to allow users to access appropriate systems and resources within the cloud environment and disable these accounts when the user no longer requires access to the resources.
- Centralized directory access – store, process, and facilitate a structured repository of information stored, mapped with unique identifiers and locations.
- Privileged user management – manage the ongoing requirements for the lifecycle of user accounts with highest privileges in the cloud environment.
- Authentication and access management – establish functional, operational, and trusted authorization and access controls to enforce security within cloud environments.
How the CCSP Certification Can Help You to Succeed
The IS2 Certified Cloud Security Professional (CCSP) is the answer to all your concerns about a robust IAM program in the cloud. CCSP is the benchmark of cloud security certifications and is repeatedly recognized as the most valued and well-rounded cloud security certification.
CCSP is a vendor-agnostic certification that ensures that certified practitioners have the security knowledge to successfully secure and protect data in any cloud environment. It is CCSP’s unique criteria that has elevated it to a standard that has allowed it to be identified as the premier cloud security certification, providing an advantage in an increasingly competitive corporate landscape.
Attaining CCSP certification shows you have the advanced technical skills and knowledge to design, manage and secure data, applications, and infrastructure in the cloud using best practices, policies, and procedures established by the cybersecurity experts at ISC2.
To learn more about how the CCSP credential can help you gain expertise and advance your career, download our white paper Cloud Security Skills Can Take Your Career to Infinity (And Beyond).
Get White Paper
.jpg?h=420&iar=0&w=420)
