
Cybersecurity has become a top concern for boards which means they’ll be looking to you for assurance and confidence. So how do you effectively communicate risk, threat, and incident response plans to a non-technical audience? This eBook shares practical tips to increase executive visibility into cyber risk—for informed decision-making.
Download NowBy Adam Kohnke, CISSP
The publicly available Cybersecurity Maturity Model Certification (CMMC) is getting a lot of attention these days, both within and outside the public sector. Developed by the U.S. Department of Defense in response to escalating cyberattacks aimed at the defense industrial base and DoD supply chain, CMMC has broader appeal for any organization determining the maturity of its IT security controls. But what, exactly, does it do to improve an organization’s cybersecurity posture?
A Model Born of Supply Chain Security
Approximately 300,000 suppliers and organizations contribute to DoD combat efforts and the DoD supply chain ecosystem, and provide services to maintain DoD systems, networks, IT system installations, IT system capabilities and other technologies. In order to protect these suppliers, defend U.S. innovation interests and bolster national security, the DoD developed the CMMC as a mechanism to assess, grade and measure the maturity of IT controls for these suppliers operating in the industrial defense sector.
The model considered non-government organizations in its formation, making it adaptable to small businesses at lower CMMC maturity levels. The DoD also paired a certification element to the CMMC model, which can either be all-encompassing or target specific segments of an organization, allowing DoD suppliers or other businesses to demonstrate their level of maturity to show federal contract compliance or attract new business.
At the highest level, the CMMC seeks to determine adequacy of controls over two specific data types:
- Federal contract information. Data that the U.S. government either directly creates or directly provides to another party to create or manage a service for the federal government. This data should not be publicly available.
- Controlled unclassified information. Non-classified data that requires processing and public release strictly follows applicable laws, regulations or government policy that further determine the data lifecycle, how it is made available and to whom. Examples include network architecture diagrams for federal systems or compensation rates for contractors.
Additionally, the CMMC wants to reduce the likelihood and proliferation of advanced persistent threats (APTs).
Data Classifications and Hierarchical Overview
The CMMC model moves one level deeper to measure cybersecurity maturity through a hierarchical assessment of domains, which are further subcategorized into processes, capabilities and capability practices. Organizational processes and capability practices are individually assessed and certified on a level of 1 to 5, with each level containing a distinct set of controls (CMMC practices) that are to be assessed and certified. (See Figures 1 and 2.)
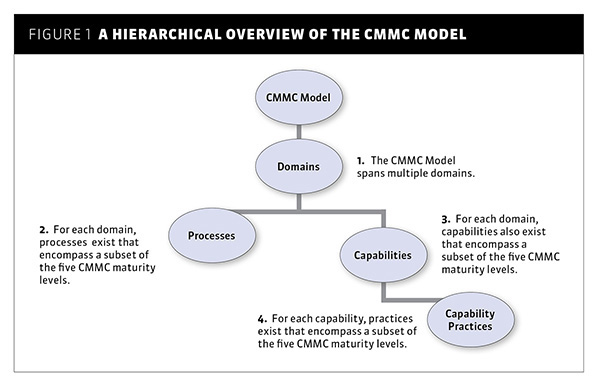
Figure 1. A hierarchical overview of the CMMC model.
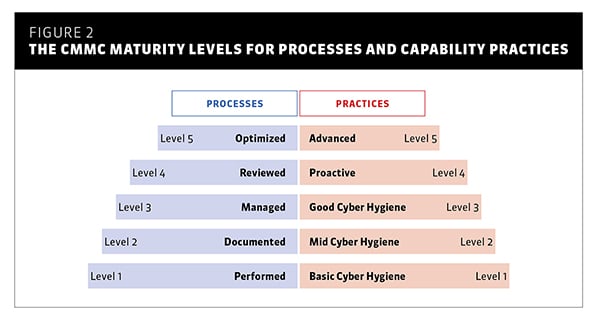
Figure 2. The CMMC maturity levels for processes and capability practices.
Each CMMC maturity level must be certified at both the Processes and Capability Practice (Practices) levels for that level of certification to apply for the organization under review. If an assessment results in an organization’s controls meeting Level 2 Processes requirements (Documented), but only certifies at Level 1 for Capability Practices (Basic Cyber Hygiene), the final result for both areas will result in certification at the lower level, in this case Level 1.
Each CMMC certification level demonstrates the company is positioned or has instituted key CMMC practices per the model requirements. Each level of maturity an organization achieves signals it is positioned to successfully protect federal contract information (Level 1), is pre-staged to protect controlled unclassified information (Level 2), is actively protecting that unclassified data (Level 3) and is positioned to reduce the presence of APTs in the environment (Levels 4-5). Now that some of the basic model elements have been described, let’s dive deeper into the inner workings of the model to see what is specifically assessed and how.
Overview of the CMMC Domains
There are 17 CMMC domains, which may be familiar to those with a federal security assessor background, as the elements are borrowed directly from FIPS 200, and NIST Special Publications 800-171 and 800-53 revision 5. Within the 17 CMMC domains, there are 43 CMMC practices, which are assessed and conceptualized at a high level. Using the Access Control domain and its four required capabilities as an example, the assessed organization should have established access control practices to form system access requirements, control internal or remote systems access, and be able to restrict access to data as it relates to users or processes. (See Figure 3.)
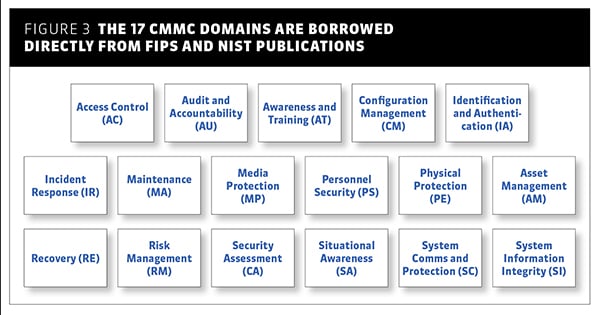
Figure 3. The 17 CMMC domains are borrowed directly from FIPS and NIST publications.
Understanding CMMC Processes
CMMC processes introduce one of the first early challenges with understanding and assessing security controls for an organization using the CMMC model. While the model does allow you to certify processes for an organization at Level 1, there are no actual process assessments performed at Level 1. (What a nice little paradox for us to mentally stumble over.)
Taking a quote directly from the federal CMMC documentation: “Level 1 requires that an organization performs the specified practices. Because the organization may only be able to perform these practices in an ad-hoc manner and may or may not rely on documentation, process maturity is not assessed for Level 1.” From an assessment perspective, this makes our job a little easier as in order to achieve Level 1 CMMC certification, as only the Level 1 practices need to be assessed and certified. CMMC processes are then assessed for maturity starting at Levels 2 through 5.
The CMMC processes are simply high-level activities that measure the extent to which an organization has formally documented policies to manage and implement CMMC practices that, in turn, govern control over and further safeguard organizational data. Using maturity levels, CMMC processes further assess the extent an organization is adequately resourcing and assessing CMMC practices as defined by policy. (See Figure 4.)
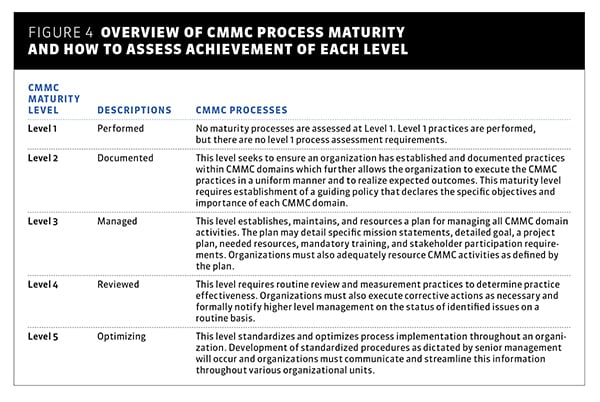
Figure 4. Overview of CMMC process maturity and how to assess achievement of each level.
Analyzing CMMC Practices
Across the five CMMC maturity levels there are a total of 171 CMMC practices. From a CMMC certification assessment perspective, this is the most labor-intensive activity, as the CMMC practices are the specific actions or key controls an organization should have implemented to protect federal contract and unclassified information or reduce likelihood and impact of APTs. A vast majority of CMMC practices (110 of 171) derive from the safeguarding and security requirements detailed in FAR Clause 52.204-21 and DFARS Clause 252.204-7012. The practices span five levels displayed in Figure 5.
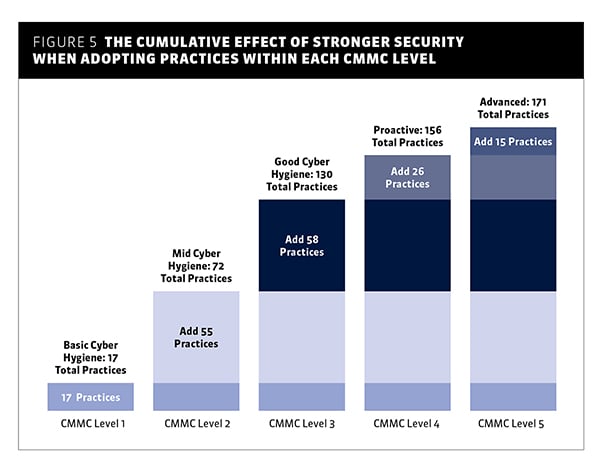
Figure 5. The cumulative effect of stronger security when adopting practices within each CMMC level.
Let’s look at an example of a CMMC practice to better understand how it might be assessed and certified, again using the Access Control (AC) domain and looking at the first Level 1 AC practice, AC.1.001:
“Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems).”
A straightforward practice is defined as one that can be quantified (number of authorized users, devices, etc.) and thoroughly assessed assuming the organization has implemented such processes. The language of all CMMC Practices follows this prescriptive control format, which is very similar to NIST-based frameworks such as Special Publication 800-53.
To become CMMC certified, organizations must have an assessment completed against all the CMMC Practices at the desired certification level and have the assessment completed by a CMMC third-party assessment organization (C3PAO). The DoD specifies all requirements for CMMC certification (if any) in the contracts it produces during Requests for Proposal (RFP) and Requests for Information (RFI). Once a CMMC certification is issued by a C3PAO, it will have a general shelf life of three calendar years from date of issuance. CMMC Level 3 certification will be required for all organizations before they can receive controlled unclassified information under any CMMC domain.
To find an approved CMMC C3PAO, the DoD has created a marketplace website where providers can be contacted and assessed. The DoD doesn’t currently allow self-certification, but does provide free self-assessment guides to download and use to prepare for CMMC certification. Currently the DoD has only made available self-assessment guides for CMMC certifications Level 1 and 3; this is likely because most organizations either need to protect federal contract information (for CMMC Level 1 certification) or controlled unclassified information (for CMMC Level 3).
Practical Guidance on Adopting the CMMC
So where to start?
First, determine what CMMC-impacted data your organization collects, stores, processes and/or transmits on behalf of federal government customers. Start with a review of all federal contracts to determine eligible information and data processing. This step also helps determine if a Level 1, Level 2 or Level 3 self-assessment is required before an external assessor begins the certification process. (See Figure 3.)
Next, obtain a self-assessment guide from the Office of the Under Secretary of Defense for Acquisition & Sustainment website and review the assessment criteria and methodology sections. External assessors are required to use the same self-assessment guides when performing certification assessments of organizations. By performing a self-assessment before the examiner, the organization will be positioned to identify control deficiencies in advance and correct them pre-emptively.
Finally, the internal self-assessment should ideally be planned, scoped and conducted by an independent department within the organization, such as enterprise risk management or the internal audit department. An alternative is to hire a third party that can certify the organization and also provide pre-certification consulting services to prepare the organization for the desired CMMC certification level. This may result in faster certification and assessment times as internal resources may need to become familiar with these new requirements that have not been assessed internally previously. The results of the self-assessment will determine time, effort and resources needed to remediate control deficiencies (if any).
To conclude, the new CMMC security framework has been released into the wild, improving upon other successful security frameworks and standards, namely FIPS 200 and NIST 800-53. CMMC leverages some familiar control components and a fairly straightforward methodology via the prescriptive assessment of security and capability practices within an organization.
The certification process had guardrails put in place via approved CMMC assessors to assist in proper certification of the organization’s security posture. Tools such as self-assessment guides are available to set up organizations for success in adopting the new framework in order to retain existing business, win new business and become more secure along the way. Time will tell how successful this new framework truly is; what remains to be seen regarding the success of CMMC involves its flexibility and adaptability in the face of emerging threats and malicious actors.
Adam Kohnke, CISSP, is the information security manager at the Infosec Institute in Madison, Wis.
References used to create this article include the following:
- High-level overview
- Model overview and descriptions
- Assessment Guide for Level 1 CMMC practices
- Introduction of core CMMC components and how they work together
- FAQs on the CMMC model and certification process
- CMMC-AB Market place to locate an approved C3PAO
- Model and assessment guide for CMMC Level 1 and 3 downloads
- Distinctions between FCI and CUI