Where Does the Buck Stop?
Many years ago U.S. President Harry Truman had a sign on his desk stating “The Buck Stops Here”. While Truman was not the originator of the sign, or the sentiment, it became associated with his presidency. This pronouncement was a bold step, indicating that his office would be the last stop when people tried to “Pass the Buck”.
In the early days of cloud computing, many unaware executives became enamored with the idea that they would no longer be responsible for any of the “headaches” associated with an on-premise data center. Things like cooling, physical security, hardware upgrades, and uninterruptable power supplies all would shift to the cloud providers. But the shifting of certain responsibilities does not also mean the shifting of accountability.
So who is responsible for what in the cloud and how can shared accountability be navigated?
Sharing is Caring
The shared responsibility model of the cloud is a nice theory and, as with all theories, it is the practical application where things can get tricky. Without guiding expertise, an unknowing executive can get lulled into thinking that passing responsibility to the cloud provider solves all of the organization’s cybersecurity problems. Shared responsibility is not the same as a transferred responsibility.
Responsibility Varies by Service
With traditional IT services, the owner is responsible for all services from networking equipment to the application itself. Cloud computing offers services such as SaaS, PaaS and IaaS to make deployment and management of computing resources more effective and efficient.
But security isn’t the same in the cloud as it is in a data center. Organizations are bound to what’s known as a “Shared Responsibility Model” where they are responsible for security “in” the cloud whereas their Cloud Service Providers (CSPs) are responsible for ensuring security “of” the cloud. These responsibilities vary depending on whether organizations are using a SaaS, PaaS or IaaS deployment.
- Infrastructure as a Service (IaaS) provides a complete infrastructure (servers and internetworking devices) and allows companies to install software on provisioned servers and control the configuration of all devices. As such, customers share responsibility with the CSP for performing security configuration and management tasks, hardening the host infrastructure and implementing network controls. The only element for which they are not at least partially responsible is ensuring the physical security of the virtual infrastructure.
- Examples include: AWS AMI, Azure Virtual Machines and GCP Compute Engine.
- Platform as a Service (PaaS) provides a computing platform and a solution stack as a service. It provides a way for customers to rent hardware, operating systems, storage, and network capacity over the internet. In this type of deployment, the CSP obviously covers more of the tasks involved with securing the cloud-based infrastructure and platform. This places greater responsibility on the enterprise to focus their energy on securing their applications, protecting their data and managing their risk.
- Examples include AWS Lamda, GCP Code Function, AWS RDS, AWS s3, GCP BigQuery and Azure SQL Database.
- Software as a Service (SaaS) providers will host and manage entire IT infrastructures which includes applications. A SaaS user does not install anything; they simply log in and use the provider’s application instance, which runs on the provider’s infrastructure. In terms of security, all they need to do is use controls such as encryption to safeguard their data against digital attackers. They can also use measures such as a principle of least privilege to control who can access their applications.
- Examples include Office365, Box, G Suite, Xero, Salesforce, Imperva WAF, Akamai CDN and Azure SQL Database.
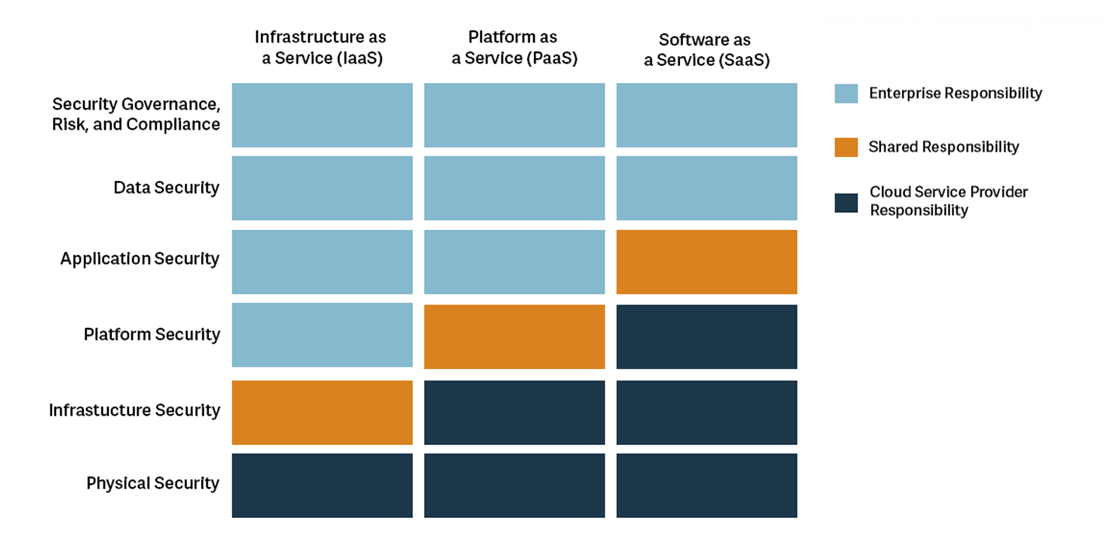
Fig. 1 Responsibility depending on type of cloud service from The Official ISC2 Guide to the CCSP CBK, 2nd Edition.
From the preceding descriptions and examples, it becomes clear that the responsibilities surrounding cloud computing security can be overwhelming to an untrained individual. Its also obvious that a cloud security professional needs to have a span of knowledge in IaaS, PaaS and SaaS to be fully able to operate and work in a cloud environment. Fortunately, in addition to platform specific training, vendor-neutral or multi-vendor training is available to prepare a person to apply security concepts across an entire cloud environment. Versatilty in the cloud is key and in many instances vendor-neutral or multi-vendor knowledge gives a professional and an organization a competitive advantage in the industry. This is because vendor-neutral knowledge can be applied across a variety of cloud platforms, increasing marketability and ensuring the ability to protect sensitive data in a global environment.
Stretching The Limits
Cloud providers often advertise their superior abilities in resiliency and adaptability, lessening downtime when compared to legacy on-premise solutions. This is largely true, different cloud offerings can provide additional benefits. With IaaS the responsibility of hardware becomes diminished for the cloud customer. Similar responsibility shifts are true PaaS and SaaS models. These models keep the customer off the upgrade treadmill, leveraging the expertise of the cloud provider.
The cloud provider is accountable for the infrastructure of the cloud under a shared responsibility model, but security incidents could put this accountability to the test. Organizations cannot afford to have their cybersecurity insurance provider deny them coverage under the logic that a ransomware event carried out by a foreign actor was an act of war, for example. They also can’t risk dealing with the ambiguities associated with human error. Rather than take the issue to court, organizations should work on avoiding these types of security incidents outright. They can do this by relying on the knowledge of skilled professionals who have knowledge about cloud security, cloud governance and risk management. These professionals can use their skills to shape their employers’ cloud security policies and provide an adequate level of defense against digital attackers. No incident, no disputed claims or court battles. And no costs (monetary or reputational) for suffering a data breach in the cloud.
So whilst the enterprise can delegate responsibility to a third party, the accountability remains fixed.
The Role Of The CISO
In most mature organizations, the security accountability rolls up to the Chief Information Security Officer (CISO). The CISO needs to both have the technical know-how and the ability to take the strategic view of cloud security. It is the CISO’s responsibility to both understand the risks of the cloud architecture and be able to develop a strategy for protecting the organization from existing and emerging threats. An important question to consider when working in a cloud environment should be “Is Your Security Team Cloud-ready?” This question could mean the difference between security success and failure in cloud implementation. A trained cloud security professional is exactly what is needed to ensure there are no surprises in a company’s cloud presence.
Working with a certified cloud security professional can help a company to make the best choices when considering a shift or operating in the cloud. A professional with specific cloud security knowledge differs from a professional with platform certification in a big way. A certification like CCSP lays foundational knowledge that is vendor-neutral and allows a professional to understand and advise on cloud security needs from the first discussions of transition to the cloud through to development and implementation. A professional with this type of foresight will help an organization ensure their cloud implementation is secure and remains secure throughout its lifecycle.
How the CCSP Can Help You Succeed
The Certified Cloud Security Professional (CCSP) credential prepares you with the most rigorous and comprehensive cloud security knowledge available. Its broad range of vendor-neutral topics and domains enables you to apply the knowledge to any cloud solution. Similar to other certifications offered by ISC2, the CCSP enjoys industry-wide recognition and gives you the ability to advise and guide your organization towards a higher cloud security profile.
Learn more about how CCSP can help advance your career in our white paper, Cloud Security Skills Can Take Your Career to Infinity (And Beyond)
Get White Paper
.jpg?h=420&iar=0&w=420)
